Enterprise & Cyber Security
Thales
We are the worldwide leader in data protection, providing everything an organization needs to protect and manage its data, identities and intellectual property – through encryption, advanced key management, tokenization, and authentication and access management. Whether it’s securing the cloud, digital payments, blockchain or the Internet of Things, security professionals around the globe rely on Thales to confidently accelerate their organization’s digital transformation. Thales Cloud Protection & Licensing is part of Thales Group.
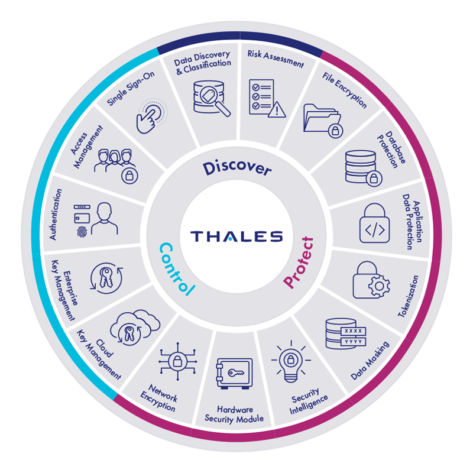
Data Protection
Thales helps organizations move past silos of encryption and crypto management solutions to attain central and uniform deployments of data protection solutions and prepare your organization for the next security challenge and new compliance requirements at the lowest TCO.
Thales advanced data discovery, data encryption, key management, network encryption, hardware security module and data protection on demand solutions enable customers to protect and remain in control of their data wherever it resides – across cloud, on-premises and hybrid IT environments.
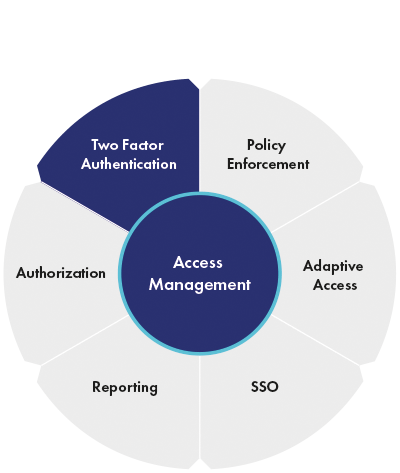
Access Management
You can monitor user access permissions and the risks associated with each login, applying step-up authentication only when the user’s context changes and the level of risk is concerning.
Access management can make life easier for workers, hiring managers, IT teams, and CISOs.
Training
Get certified and learn from the most experienced trainers.
